-

Bracing for Interference: Electronic Warfare and its Spillover Effects
-
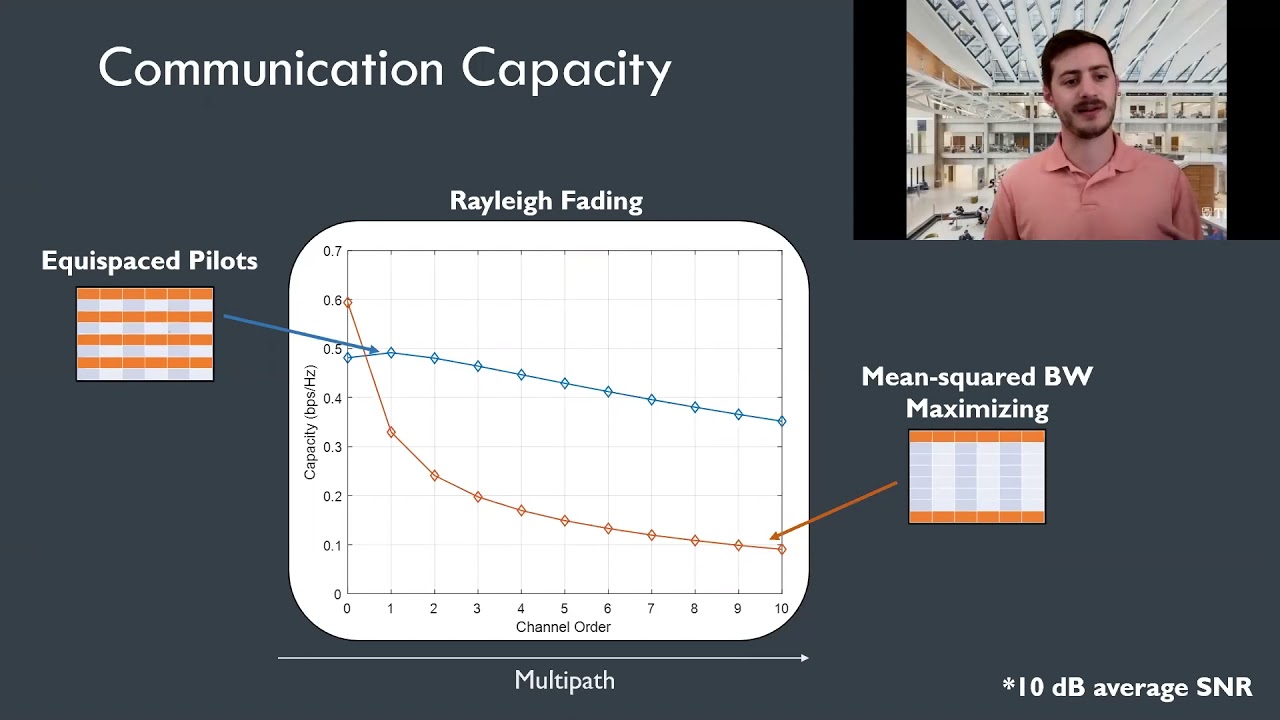
Purposeful OFDM Co-Design for Ranging and Communications
-

Multi-Antenna Vision-and-Inertial Aided CDGNSS for Micro Aerial Vehicle Pose Estimation
Paper referenced in the presentation: Multi-Antenna Vision-and-Inertial Aided CDGNSS for Micro Aerial Vehicle Pose Estimation
-

Fused LEO GNSS
Paper referenced in the presentation: Fused Low-Earth-Orbit GNSS
-
Vehicle Sensorium Demonstration
-

Open-World Virtual Reality Headset Tracking
Paper referenced in the presentation: Open-World Virtual Reality Headset Tracking
-

Game-Theoretic Counter-UAV for Real-World Situations
Paper referenced in the presentation: Intercepting Unmanned Aerial Vehicle Swarms with Neural-Network-Aided Game-Theoretic Target Assignment
-

All-Weather sub-50-cm Radar-Inertial Positioning
Paper referenced in the presentation: All-Weather sub-50-cm Radar-Inertial Positioning
-

A Proposal for Securing Terrestrial Radio-Navigation Systems
Paper referenced in the presentation: A Proposal for Securing Terrestrial Radio-Navigation Systems
-

Long Range, Low SWaP-C FMCW Radar
Paper referenced in the presentation: Long Range, Low SWaP-C Radar
-

Automotive Collision Risk Estimation Under Cooperative Sensing (ICASSP 2020)
Paper referenced in the presentation: Automotive Collision Risk Estimation Under Cooperative Sensing
-
Cooperative Sensing for Automated Vehicles
July 2020 presentation for U.C. Berkeley's SemiAutonomous Seminar Series
-

Open World Virtual Reality (OWVR)
-

New Aerial Robotics Course
-

Drones battle to pop balloons in UT course
-

Keeping the car in its lane
Precise GPS allows automated cars to know thier own position with a high degree of accuracy, which is imperative for keeping a car in its own lane. Take a look at our latest papers on the topic:
-

Centimeter-Accurate Mobile Positioning
Researchers at UT are discovering ways to make centimeter-accurate GPS affordable, reliable, and marketable, with some exciting possibilities for consumers. Take a look at our latest papers on the topic:
A Dense Reference Network for Mass-Market Centimeter-Accurate Positioning
Advanced Techniques for Centimeter-Accurate GNSS Positioning on Low-Cost Mobile Platforms
-
Super GPS brings autonomous cars closer to reality
Researchers at UT are now actively testing the precise GPS on vehicles. Take a look at our latest papers on the topic:
A Dense Reference Network For Mass Market Centimeter Accurate Positioning
On the Feasibility of cm-Accurate Positioning via a Smartphone's Antenna and GNSS Chip -

UT researchers build drone dome
The goal of the Machine Games project is to make drones a part of everyday life. Drones will use cm-accurate positioning service enabled by concurrent research at UT Radionavigation Lab. Take a look at our latest paper on the topic:
A Dense Reference Network For Mass Market Centimeter Accurate Positioning -

Austin the first city in the world to test out Precise GPS
Researchers at UT are working to make Austin the first city to support this type of technology. Take a look at our latest papers on the topic:
A Dense Reference Network For Mass Market Centimeter Accurate Positioning
On the Feasibility of cm-Accurate Positioning via a Smartphone's Antenna and GNSS Chip -

Techniques for Spoofing and for Spoofing Mitigation
In November, 2015, Dr. Mark Psiaki from Cornell University gave a presentation on GNSS spoofing and spoofing mitigation at the International Symposium on Navigation and Timing, ENAC Toulouse, France. This talk features the collaboration on GNSS security research between Mark's research group at Cornell University and the UT Radionavigation Laboratory. It is the most comprehensive presentation on the topic of GNSS security to date, and serves as a verbal companion to Psiaki's and Humphreys's 2016 IEEE Proceedings paper "GNSS Spoofing and Detection"
-

Seminar on
Dr. Todd Humphreys delivered a seminar on Low-Cost Centimeter-Accurate Mobile Positioning at the Roadway Safety Institute at University of Minnesota. This presentation focused on techniques for reducing the initialization time for centimeter-accurate positioning on mobile devices. It further examined technical and market prerequisites for improved safety for semi-autonomous and autonomous vehicles, globally registered augmented and virtual reality, and crowd-sourced three-dimensional mapping.
-

Centimeter-Accurate GPS Demo
Using software developed at RNL and a low-cost GPS antenna, we demonstrate position tracking of a virtual reality headset to centimeter accuracy, in real time.
-

Spoofing on the High Seas
Todd Humphreys is the Director of the Radionavigation Lab at the University of Texas at Austin, where he is also an Assistant Professor of Aerospace Engineering. As one of the world's leading experts on GPS technology, Dr. Humphreys caught the attention of the U.S. Department of Homeland Security for his recent research on defending against intentional GPS jamming of drones over U.S. airspace.
On this episode of Game Changers, Professor Humphreys addresses the current use and future potential of GPS technology.
-

Game Changers: The Future of GPS
Todd Humphreys is the Director of the Radionavigation Lab at the University of Texas at Austin, where he is also an Assistant Professor of Aerospace Engineering. As one of the world's leading experts on GPS technology, Dr. Humphreys caught the attention of the U.S. Department of Homeland Security for his recent research on defending against intentional GPS jamming of drones over U.S. airspace.
On this episode of Game Changers, Professor Humphreys addresses the current use and future potential of GPS technology.
-
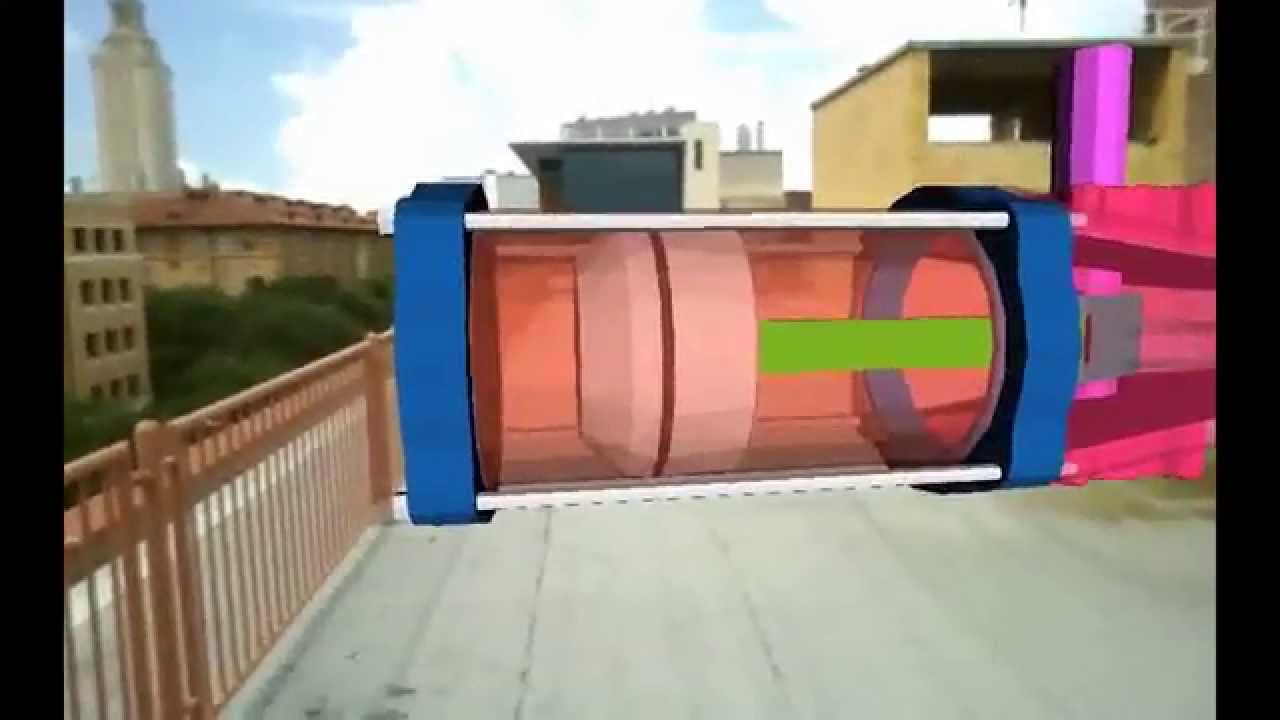
Precise Augmented Reality Enabled by Carrier-Phase Differential GPS
We're developing an extremely precise augmented reality (AR) system based on carrier-phase differential GPS (CDGPS). The system provides precise position and attitude, which can be used to display position- and attitude-specific objects and information in real-time. The video below, dubbed "Pillars and Piston," is a first demonstration of our system's capability.
-
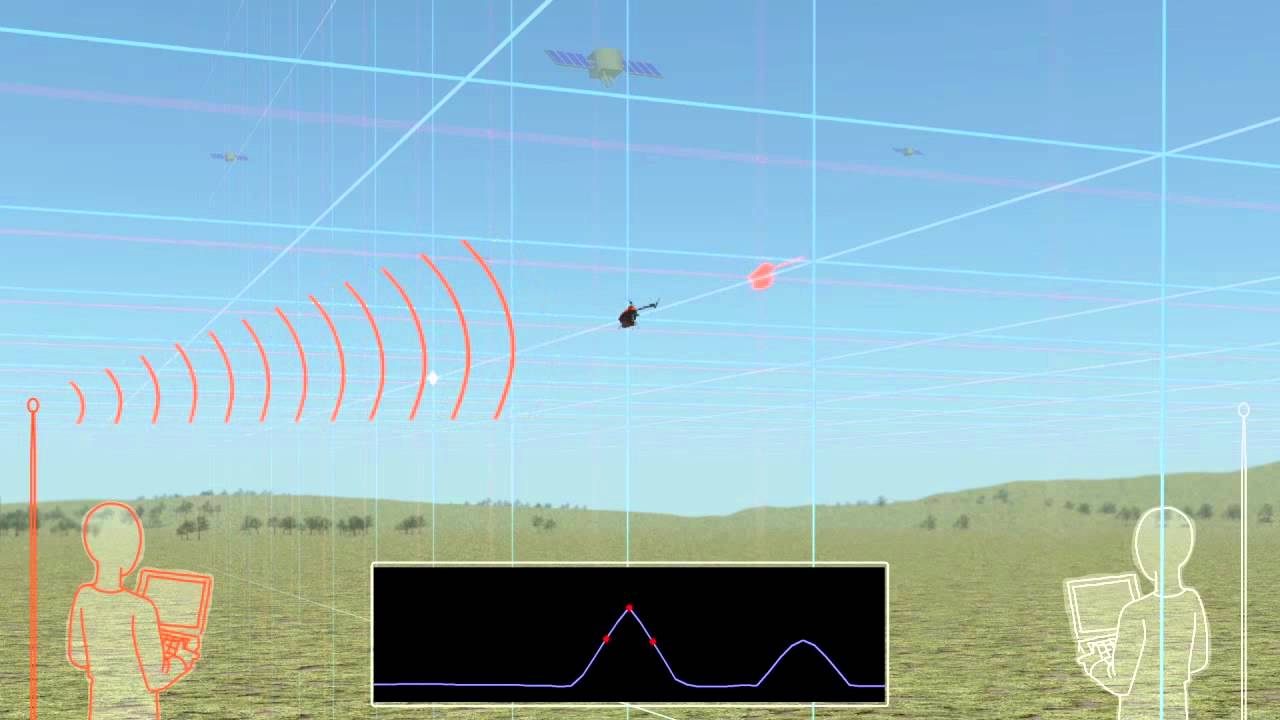
Drone Capture Congressional Testimony Video
This video illustrates the steps taken for successful drone capture. An earlier version of this video appeared in Dr. Humphrey's testimony to Congress in July 2012.
-
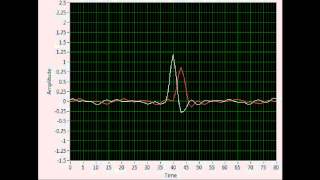
Tracking Loop Carry Off
We demonstrate here the response of a GPS receiver's tracking loops to a spoofing attack. The receiver's correlation function is displayed along a grid of taps about the peak. The white trace is the in-phase component and the red is the quadrature component, where phase is compared to the prompt tap which is aligned with the correlation peak.
-
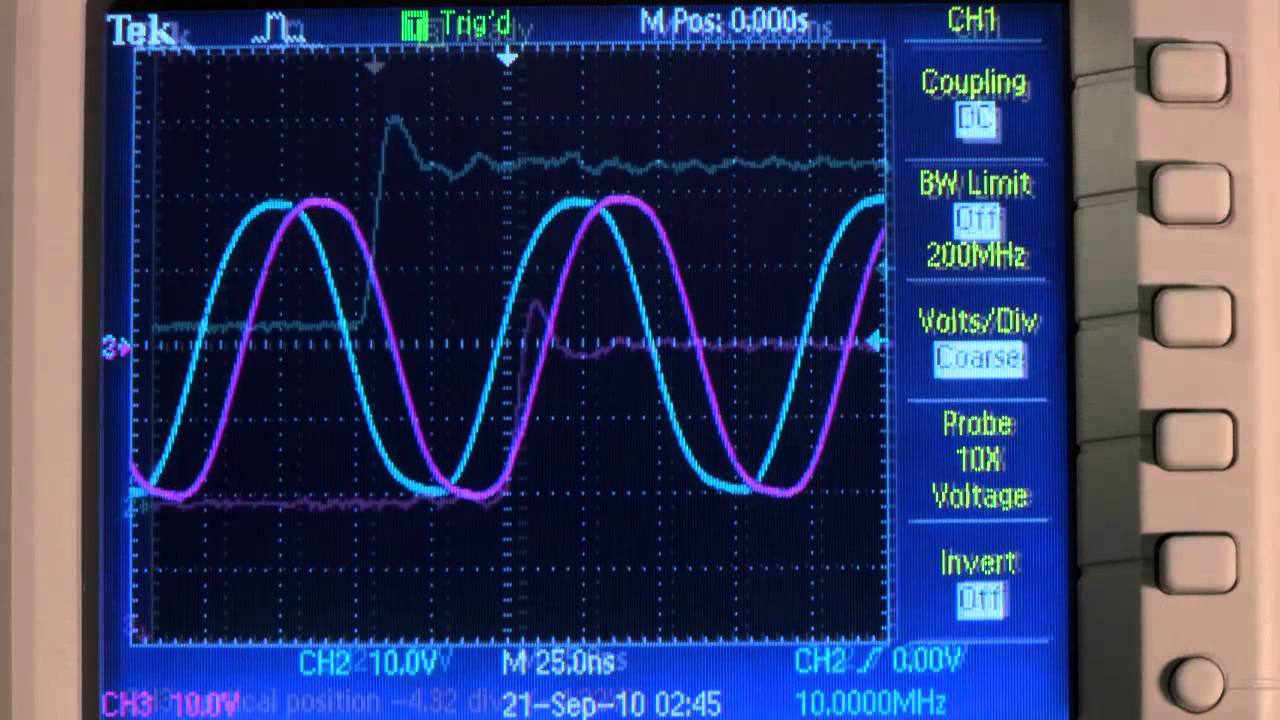
Spoofing a GPS Time Reference Receiver and Phasor Measurement Unit
We demonstrate here a spoofing attack against a GPS time reference receiver like those used for time synchronization in cell phone base stations. We also demonstrate a spoofing attach against a phasor measurement unit designed to synchronize the power grid. Download the video here (right click, save as) [70 MB].
To learn more about the Radionavigation Lab's civil GPS spoofer see the paper or the presentation.
-
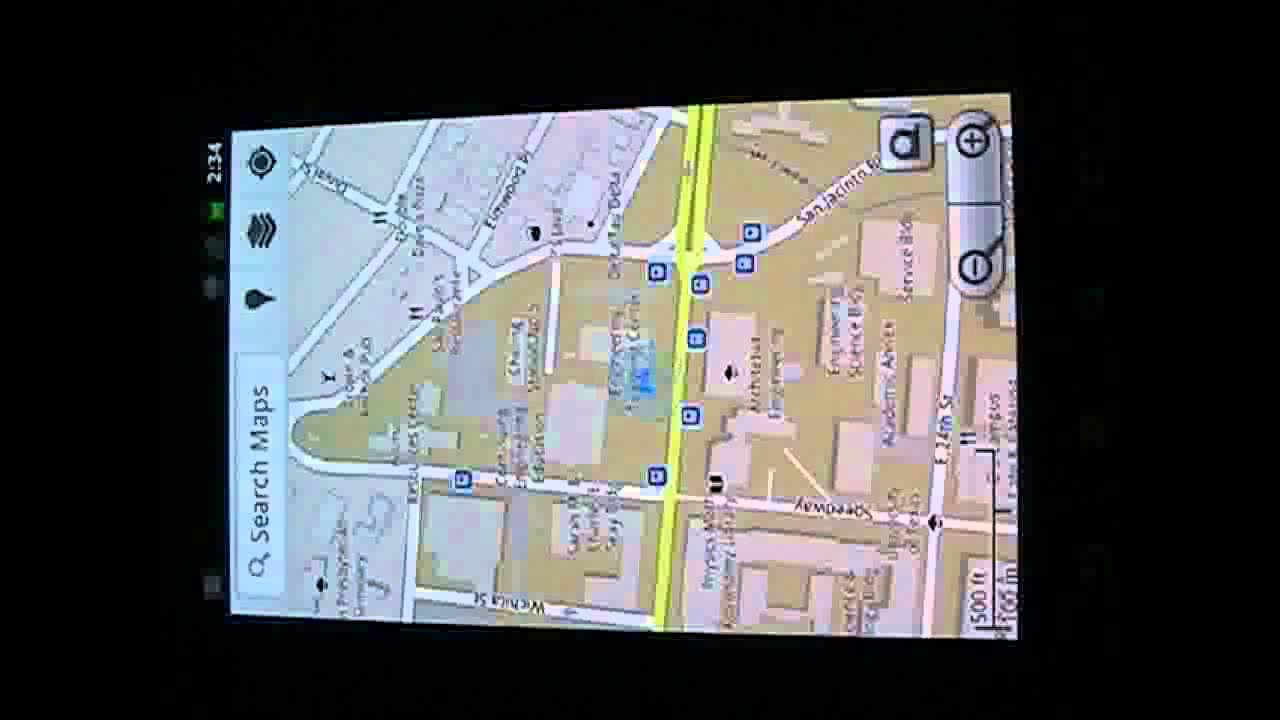
Spoofing Attack on Android
An Android's GPS unit being spoofed with the Radionavigation Lab's civil GPS spoofer. For more information on the spoofer see the paper or the presentation.
-
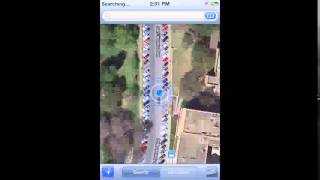
Spoofing Attack on iPhone
An iPhone's GPS unit being spoofed with the Radionavigation Lab's civil GPS spoofer. For more information on the spoofer see the paper or the presentation.
-
Internal Footage of a Live Spoofing Attack
The autocorrelation function of a GPS tracking channel under a spoofing attack.
-
Bracing for Interference: Electronic Warfare and its Spillover Effects 

-
Purposeful OFDM Co-Design for Ranging and Communications 

-
Multi-Antenna Vision-and-Inertial Aided CDGNSS for Micro Aerial Vehicle Pose Estimation Paper referenced in the presentation: Multi-Antenna Vision-and-Inertial Aided CDGNSS for Micro Aerial Vehicle Pose Estimation


-
Fused LEO GNSS Paper referenced in the presentation: Fused Low-Earth-Orbit GNSS


-
Vehicle Sensorium Demonstration 

-
Open-World Virtual Reality Headset Tracking Paper referenced in the presentation: Open-World Virtual Reality Headset Tracking


-
Game-Theoretic Counter-UAV for Real-World Situations Paper referenced in the presentation: Intercepting Unmanned Aerial Vehicle Swarms with Neural-Network-Aided Game-Theoretic Target Assignment


-
All-Weather sub-50-cm Radar-Inertial Positioning Paper referenced in the presentation: All-Weather sub-50-cm Radar-Inertial Positioning


-
A Proposal for Securing Terrestrial Radio-Navigation Systems Paper referenced in the presentation: A Proposal for Securing Terrestrial Radio-Navigation Systems


-
Long Range, Low SWaP-C FMCW Radar Paper referenced in the presentation: Long Range, Low SWaP-C Radar


-
Automotive Collision Risk Estimation Under Cooperative Sensing (ICASSP 2020) Paper referenced in the presentation: Automotive Collision Risk Estimation Under Cooperative Sensing


-
Cooperative Sensing for Automated Vehicles July 2020 presentation for U.C. Berkeley's SemiAutonomous Seminar Series


-
Open World Virtual Reality (OWVR) 

-
New Aerial Robotics Course 

-
Drones battle to pop balloons in UT course 

-
Keeping the car in its lane Precise GPS allows automated cars to know thier own position with a high degree of accuracy, which is imperative for keeping a car in its own lane. Take a look at our latest papers on the topic:


-
Centimeter-Accurate Mobile Positioning Researchers at UT are discovering ways to make centimeter-accurate GPS affordable, reliable, and marketable, with some exciting possibilities for consumers. Take a look at our latest papers on the topic:
A Dense Reference Network for Mass-Market Centimeter-Accurate Positioning
Advanced Techniques for Centimeter-Accurate GNSS Positioning on Low-Cost Mobile Platforms


-
Super GPS brings autonomous cars closer to reality Researchers at UT are now actively testing the precise GPS on vehicles. Take a look at our latest papers on the topic:
A Dense Reference Network For Mass Market Centimeter Accurate Positioning
On the Feasibility of cm-Accurate Positioning via a Smartphone's Antenna and GNSS Chip

-
UT researchers build drone dome The goal of the Machine Games project is to make drones a part of everyday life. Drones will use cm-accurate positioning service enabled by concurrent research at UT Radionavigation Lab. Take a look at our latest paper on the topic:
A Dense Reference Network For Mass Market Centimeter Accurate Positioning

-
Austin the first city in the world to test out Precise GPS Researchers at UT are working to make Austin the first city to support this type of technology. Take a look at our latest papers on the topic:
A Dense Reference Network For Mass Market Centimeter Accurate Positioning
On the Feasibility of cm-Accurate Positioning via a Smartphone's Antenna and GNSS Chip

-
Techniques for Spoofing and for Spoofing Mitigation In November, 2015, Dr. Mark Psiaki from Cornell University gave a presentation on GNSS spoofing and spoofing mitigation at the International Symposium on Navigation and Timing, ENAC Toulouse, France. This talk features the collaboration on GNSS security research between Mark's research group at Cornell University and the UT Radionavigation Laboratory. It is the most comprehensive presentation on the topic of GNSS security to date, and serves as a verbal companion to Psiaki's and Humphreys's 2016 IEEE Proceedings paper "GNSS Spoofing and Detection"


-
Seminar on Dr. Todd Humphreys delivered a seminar on Low-Cost Centimeter-Accurate Mobile Positioning at the Roadway Safety Institute at University of Minnesota. This presentation focused on techniques for reducing the initialization time for centimeter-accurate positioning on mobile devices. It further examined technical and market prerequisites for improved safety for semi-autonomous and autonomous vehicles, globally registered augmented and virtual reality, and crowd-sourced three-dimensional mapping.


-
Centimeter-Accurate GPS Demo Using software developed at RNL and a low-cost GPS antenna, we demonstrate position tracking of a virtual reality headset to centimeter accuracy, in real time.


-
Spoofing on the High Seas Todd Humphreys is the Director of the Radionavigation Lab at the University of Texas at Austin, where he is also an Assistant Professor of Aerospace Engineering. As one of the world's leading experts on GPS technology, Dr. Humphreys caught the attention of the U.S. Department of Homeland Security for his recent research on defending against intentional GPS jamming of drones over U.S. airspace.
On this episode of Game Changers, Professor Humphreys addresses the current use and future potential of GPS technology.


-
Game Changers: The Future of GPS Todd Humphreys is the Director of the Radionavigation Lab at the University of Texas at Austin, where he is also an Assistant Professor of Aerospace Engineering. As one of the world's leading experts on GPS technology, Dr. Humphreys caught the attention of the U.S. Department of Homeland Security for his recent research on defending against intentional GPS jamming of drones over U.S. airspace.
On this episode of Game Changers, Professor Humphreys addresses the current use and future potential of GPS technology.


-
Precise Augmented Reality Enabled by Carrier-Phase Differential GPS We're developing an extremely precise augmented reality (AR) system based on carrier-phase differential GPS (CDGPS). The system provides precise position and attitude, which can be used to display position- and attitude-specific objects and information in real-time. The video below, dubbed "Pillars and Piston," is a first demonstration of our system's capability.


-
Drone Capture Congressional Testimony Video This video illustrates the steps taken for successful drone capture. An earlier version of this video appeared in Dr. Humphrey's testimony to Congress in July 2012.


-
Tracking Loop Carry Off We demonstrate here the response of a GPS receiver's tracking loops to a spoofing attack. The receiver's correlation function is displayed along a grid of taps about the peak. The white trace is the in-phase component and the red is the quadrature component, where phase is compared to the prompt tap which is aligned with the correlation peak.


-
Spoofing a GPS Time Reference Receiver and Phasor Measurement Unit We demonstrate here a spoofing attack against a GPS time reference receiver like those used for time synchronization in cell phone base stations. We also demonstrate a spoofing attach against a phasor measurement unit designed to synchronize the power grid. Download the video here (right click, save as) [70 MB].
To learn more about the Radionavigation Lab's civil GPS spoofer see the paper or the presentation.


-
Spoofing Attack on Android An Android's GPS unit being spoofed with the Radionavigation Lab's civil GPS spoofer. For more information on the spoofer see the paper or the presentation.


-
Spoofing Attack on iPhone An iPhone's GPS unit being spoofed with the Radionavigation Lab's civil GPS spoofer. For more information on the spoofer see the paper or the presentation.


-
Internal Footage of a Live Spoofing Attack The autocorrelation function of a GPS tracking channel under a spoofing attack.




